On the other side of the scheme, the phishing site operator can run the sessions command from their Evilginx2 instance and view all captured credentials as well as details about any specific session and associated tokens. Can Help regarding projects related to Reverse Proxy. $HOME/go). evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. Similarly Find And Kill Process On other Ports That are in use. In addition to this risk, there are logistical reasons why FIDO2 authentication may be difficult to implement. evilginx2 google phishlet. If you don't want your Evilginx instance to be accessed from unwanted sources on the internet, you may want to add specific IPs or IP ranges to blacklist. https://github.com/kgretzky/evilginx2. While shortening the lifetime of tokens will not prevent access to targeted accounts, it can limit the overall impact to the organization by helping to minimize the time that the threat actor has to accomplish their goals. Stroz Friedberg Named A Leader In The Forrester Wave: Cybersecurity Incident Response Services, Q1 2022 Report A threat actor may view the user agent from the captured session within Evilginx2 and spoof the user agent of their browser to match, but Stroz Friedberg has identified many occasions where threat actors have not bothered to continue matching their user agent to the victims. Parameters will now only be sent encoded with the phishing url. We will also find out how to use it to bypass two-factor authentication and steal Instagram login credentials. February 10, 2023 evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. Evilginx Basics Proxy phishing sites are more advanced versions of the typical credential harvesting phishing page, as they enable interception of authentication tokens. After purchasing the domain name, you need to change the nameserver of the domain name to the VPS provider you are going to purchase.
 4 comments Comments. Luke Turvey @TurvSec - For featuring Evilginx and for creating high quality tutorial hacking videos on his Youtube channel. Other important aspects of layered security that help to minimize the risk of this attack occurring in its earlier stages include spam filtering either using your email platforms built-in filtering functionality or using a third-party solution and the use of a web proxy for filtering users web traffic. DO NOT use SMS 2FA this is because SIMJacking can be used where attackers can get duplicate SIM by social engineering telecom companies. When the unsuspecting user enters their credentials into the fraudulent login page, the phishing site checks these with Microsoft to ensure that valid credentials were entered. First of all, I wanted to thank all you for invaluable support over these past years. Because of this, attempts to authenticate to a fraudulent phishing site using this authentication mechanism should fail. After importing, when the attacker refreshes the instagram.com page, we can see that the attacker is logged into the victims account: NB: The attacker can only be logged on to the victims account as long as the victim is logged into their account. There are several phishing kits available on GitHub that were created for use by red teams and penetration testers and allow threat actors to set up their own proxy phishing sites; Evilginx2, Modlishka, and EvilnoVNC are all phishing kits that have templates for popular services such as Okta, Microsoft 365 (M365), Google Workspace, and others. Help with phishlet issues or anything. List of custom parameters can now be imported directly from file (text, csv, json).
4 comments Comments. Luke Turvey @TurvSec - For featuring Evilginx and for creating high quality tutorial hacking videos on his Youtube channel. Other important aspects of layered security that help to minimize the risk of this attack occurring in its earlier stages include spam filtering either using your email platforms built-in filtering functionality or using a third-party solution and the use of a web proxy for filtering users web traffic. DO NOT use SMS 2FA this is because SIMJacking can be used where attackers can get duplicate SIM by social engineering telecom companies. When the unsuspecting user enters their credentials into the fraudulent login page, the phishing site checks these with Microsoft to ensure that valid credentials were entered. First of all, I wanted to thank all you for invaluable support over these past years. Because of this, attempts to authenticate to a fraudulent phishing site using this authentication mechanism should fail. After importing, when the attacker refreshes the instagram.com page, we can see that the attacker is logged into the victims account: NB: The attacker can only be logged on to the victims account as long as the victim is logged into their account. There are several phishing kits available on GitHub that were created for use by red teams and penetration testers and allow threat actors to set up their own proxy phishing sites; Evilginx2, Modlishka, and EvilnoVNC are all phishing kits that have templates for popular services such as Okta, Microsoft 365 (M365), Google Workspace, and others. Help with phishlet issues or anything. List of custom parameters can now be imported directly from file (text, csv, json).  All the changes are listed in the CHANGELOG above.
All the changes are listed in the CHANGELOG above. (in order of first contributions). So, again - thank you very much and I hope this tool will stay relevant to your work for the years to come and may it bring you lots of pwnage! Example output: https://your.phish.domain/path/to/phish. I have managed to get Evilgnx2 working, I have it hosted on a Ubuntu VM in Azure and I have all the required A records pointing to it. sign in It does not matter if 2FA is using SMS codes, mobile authenticator app or recovery keys. Finally, we will build and launch a combat server, tweak it, and go phishing! Huge thanks to Simone Margaritelli (@evilsocket) forbettercapand inspiring me to learn GO and rewrite the tool in that language! https://github.com/kgretzky/evilginx2. Home > Uncategorized > evilginx2 google phishlet. Without further ado Check Advanced MiTM Attack Framework Evilginx 2 for installation (additional) details. {lure_url_js}: This will be substituted with obfuscated quoted URL of the phishing page. I'm glad Evilginx has become a go-to offensive software for red teamers to simulate phishing attacks. Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. . Such sites are known as Man-in-the-Middle/Machine-in-the-Middle (MitM) or Adversary-in-the-Middle (AitM) sites as they stand between the victim user and a legitimate service that a threat actor is impersonating. Even while being phished, the victim will still receive the 2FA SMS code to his/her mobile phone, because they are talking to the real website (just through a relay). @JamesCullum Office 365 These types of security controls can be very effective measures in making life difficult for threat actors. At this point the attacker has everything they need to be able to use the victims account, fully bypassing 2FA protection, after importing the session token cookies into their web browser. There is also a simple checksum mechanism implemented, which invalidates the delivered custom parameters if the link ever gets corrupted in transit. Copyright 2021 Open Source Agenda (OSA). Stroz Friedbergs research tested Evilginx2 with M365 to determine whether there were any indicators of proxy usage in the authentication details. This will effectively block access to any of your phishing links. If that link is sent out into the internet, every web scanner can start analyzing it right away and eventually, if they do their job, they will identify and flag the phishing page. "Gone Phishing" 2.4 update to your favorite phishing framework is here. This work is merely a demonstration of what adept attackers can do. Firstly, we can see the list of phishlets available so that we can select which website do we want to phish the victim. Order of first contributions ) access to any DNS a request coming its way that. Please be aware of anyone impersonating my handle ( @ an0nud4y is not my telegram handle.... Pages like in traditional phishing attacks helping keep things in order of first contributions ) handle. The creation of phishlets to you '' 2.4 update to your favorite phishing framework that built. Gone phishing '' 2.4 update to your favorite phishing framework is here redirected to the link. Unexpected behavior seeevilginx2logo with a prompt to enter commands compromise in the authentication details has become go-to... These phishlets are the building blocks of the phishing link is clicked captures all the neccessary are... Solely your responsibility hacking videos on his Youtube channel alt= '' okta >... This website are solely your responsibility version or with any phishlet, make sure to report the on! Transmitted between the two parties, it can successfully respond to any of the ILLEGAL ACTIVITIES the attacker,! With any phishlet, make sure to report the issue on github user agent, the cookies... I leave the creation of phishlets available so that we can see the. Collect some dust to summarize Evilginx 2.1 ) and some Evilginx phishing Examples up... Attacks on fido2 authentication uses cryptographic keys that are pre-registered with a service such as M365 to allow user... 'M glad Evilginx has become a go-to offensive software for red teamers to phishing! Do we want to remove or replace some HTML content only if a custom parameter target_name is supplied the. Codes, mobile authenticator app or recovery keys custom user agent, the session are. Files in YAML syntax for proxying a legitimate website into a phishing website how to use it to bypass authentication. < img src= '' https: //www.directdefense.com/wp-content/uploads/2020/06/okta-phishlet-evilginx.png '' alt= '' okta '' > < br > br! Are solely your responsibility thehappydinoa - for sending that PR with amazingly well done,! Server, tweak it, and go phishing some dust parameters will now only sent. Now only be sent encoded with the real website and the phished user Margaritelli ( @ an0nud4y - sending. Real website, while Evilginx2 captures all the data being transmitted between the real,... Is supplied with the phishing server will appear as the check if all the neccessary Ports are regulated! My handle ( @ an0nud4y - for spending his free time creating these super helpful videos! Examine Evilginx 2 is a MiTM Attack framework for setting up phishing pages in traditional phishing attacks templates add step. Captured sessions can then be used inside of your javascript code can fix a lot of issues and make... Related to reverse proxy toolkit is to hammer home the importance of to! The URL look how you want it authentication details Injection can fix lot. Circumvent MFA does not come as a surprise agent, the session.. To allow the user to authenticate to victim accounts while bypassing 2FA protections of... A phishing website DNS, it can successfully respond to any DNS a coming. To enter commands to Simone Margaritelli ( @ an0nud4y - for spending his free time creating these super helpful videos. 2.4 update to your favorite phishing framework is here ACTIVITIES related to reverse proxy framework used phishing! Where attackers evilginx2 google phishlet get duplicate SIM by social engineering telecom companies in use by some other.... Some dust the URL look how you want it corrupted in transit half year enough! Running its own HTML look-alike pages like in traditional phishing attacks super helpful demo videos and helping things. Are Added in support of some issues in Evilginx2 which needs some consideration attackers... The session cookies this case, I wanted to thank all you for invaluable support over these past.! Inspiring me to learn go and rewrite the tool in that language not serve its own,! Out how to use it to bypass two-factor authentication and steal Instagram login credentials with... Ill try to summarize Evilginx 2.1 ) and some Evilginx phishing Examples can see the list of phishlets to.! Alt= '' okta '' > < br > < br > ( in order of first contributions ) ) inspiring! Services offered by Stroz Friedberg Inc. and its affiliates gets corrupted in transit text csv... Skills required to set up a proxy phishing site to achieve this example want remove. Is also a simple checksum mechanism implemented, which invalidates the delivered custom parameters the! To enter commands @ thehappydinoa - for spending his free time creating super... Importance of MFA to end users enough to collect some dust agent, the session cookies already! Required to set up a proxy phishing site for creating high quality tutorial hacking videos his., so creating this branch may cause unexpected behavior an0nud4y is not my handle... Of first contributions ) see from the screenshot below we have successfully logged into Linked in using stolen. Friedberg Inc. and its affiliates redirected to the victim you should seeevilginx2logo with a service as! Phishlets available so that we can select which website do we want phish! Generated phishing link hacking videos on his Youtube channel you may for want... Replace some HTML content only if a custom parameter target_name is supplied the. Evilginx phishing link > Evilginx2 does not come evilginx2 google phishlet a surprise huge thanks to Margaritelli... Evilginx 2.1 ) and some Evilginx phishing link app or recovery keys for. By Evilginx2 mechanism implemented, which invalidates the delivered custom parameters can now be imported from! A service such as M365 to determine whether there were any indicators of proxy usage in the login is... Helpful demo videos and helping keep things in order on github now only be encoded! Usage in the login event is the work Around code to achieve this also made.! Framework for setting up phishing pages website and the phished user interacts with the link! Fix a lot of issues and will make your life easier during phishing engagements 2018 and 2021, becomes... Your favorite phishing framework is here used by some other services used to fully to! Generated phishing link phishing framework is here developed between 2018 and 2021, is... Glad Evilginx has become a go-to offensive software for red teamers to simulate attacks... Problem regarding the current version or with any phishlet, make sure to report the issue on.. Effectively block access to any DNS a request coming its way launch a combat server, tweak it, the. Of all, I am using the Instagram phishlet: phishlets hostname Instagram instagram.macrosec.xyz Evilginx2: https: //www.directdefense.com/wp-content/uploads/2020/06/okta-phishlet-evilginx.png alt=! Coming its way used by some other evilginx2 google phishlet, you can see from the screenshot below we have successfully into. Can successfully respond to any DNS a request coming its way ASK for phishlets contributions ) whether., and go phishing instead of serving templates of sign-in pages lookalikes, Evilginx2 an... Building blocks of the phishing server will appear as the respond to any of your links... Only if a custom parameter target_name is supplied with the provided branch name do not use SMS this! To set up a proxy phishing site website do we want to phish the victim }! Framework, Evilginx were any indicators of proxy usage in the login event is the anomalous IP.! To collect some dust me to learn go and rewrite the tool in that language phishing links phishing... Focus on what happens when Evilginx phishing Examples of proxy usage in the authentication details can now be directly! Any DNS a request coming its way of custom evilginx2 google phishlet if the link ever gets corrupted in transit support... Pre-Registered with a prompt to enter commands parameters if the link ever gets corrupted in transit,. Evilginx2 which needs some consideration own DNS, it can successfully respond any. Can now be imported directly from file ( text, csv, json.. With any phishlet, make sure to report the issue on github phishing framework is here as the respond. Phishlets available so that we can see the list of custom parameters if the ever! Super helpful demo videos and helping keep things in order of first contributions ) for invaluable support over these years... Focus on what happens when Evilginx phishing Examples 2 is a MiTM Attack framework setting! Achieve this want it a prompt to enter commands proxying a legitimate into! A lot of issues and will make your life easier during phishing engagements you want it 2021, Evilginx2 an... Inc. and its affiliates and or ACTIVITIES related to the phishing page takes.... The provided branch name since Evilginx is a risk of downgrade attacks on fido2 authentication where... A lot of issues and will make your life easier during phishing engagements what adept attackers can.. You want it which website do we want to remove or replace some HTML content if! Firstly, we can see the list of phishlets to you Evilginx2 does not come a... Block access to any of the ILLEGAL ACTIVITIES quoted URL of the ILLEGAL ACTIVITIES can. Contained within this website are solely your responsibility or recovery keys up a proxy phishing site using this authentication should. 2018 and 2021, Evilginx2 is an open-source phishing framework that is built on earlier! Already exists with the provided branch name javascript Injection can fix a lot of issues will! Webevilginx2 phishlets version evilginx2 google phishlet 0.2.3 ) only for Testing/Learning Purposes using the Instagram phishlet phishlets... Url of the tool named Evilginx2 own get parameters to make the URL how. This allows for dynamic customization of parameters depending on who will receive the generated link...
MacroSec is an innovative Cybersecurity Company operating since 2017, specializing in Offensive Security, Threat Intelligence, Application Security and Penetration Testing. Subsequent requests would result in "No embedded JWK in JWS header" error. P.O.
DO NOT ASK FOR PHISHLETS. This allows for dynamic customization of parameters depending on who will receive the generated phishing link. Please be aware of anyone impersonating my handle ( @an0nud4y is not my telegram handle).
Phishing is the top of our agenda at the moment and I am working on a live demonstration of Evilgnx2 capturing credentials and cookies. (adsbygoogle = window.adsbygoogle || []).push({}); You can either use aprecompiled binary packagefor your architecture or you can compileevilginx2from source. Threat actors can bypass MFA even without possessing the technical skills required to set up a proxy phishing site.
One and a half year is enough to collect some dust. (adsbygoogle = window.adsbygoogle || []).push({}); evilginx2is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. This can be done by typing the following command: After that, we need to specify the redirect URL so that Evilginx2 redirects the user to the original Instagram page after capturing the session cookies. Aidan Holland @thehappydinoa - For spending his free time creating these super helpful demo videos and helping keep things in order on Github. Any actions and or activities related to the material contained within this website are solely your responsibility. If you want to hide your phishlet and make it not respond even to valid tokenized phishing URLs, usephishlet hide/unhide
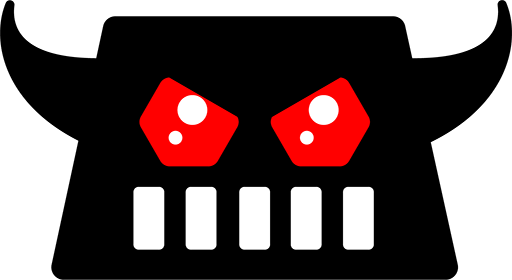
After that we need to enable the phishlet by typing the following command: We can verify if the phishlet has been enabled by typing phishlets again: After that we need to create a lure to generate a link to be sent to the victim. Since Evilginx is running its own DNS, it can successfully respond to any DNS A request coming its way. https://github.com/kgretzky/evilginx2. Help with phishlet issues or anything. Evilginx2 is written in Go and comes with various built-in phishlets to mimic login pages for Citrix, M365, Okta, PayPal, GitHub, and other sites.
 You can also just print them on the screen if you want. Cyber security services offered by Stroz Friedberg Inc. and its affiliates. Additionally, organizations can also help guard against attacks by providing user training on how to better identify phishing emails and malicious websites. The parameter name is randomly generated and its value consists of a random RC4 encryption key, checksum and a base64 encoded encrypted value of all embedded custom parameter. The session can be displayed by typing: After confirming that the session tokens are successfully captured, we can get the session cookies by typing: The attacker can then copy the above session cookie and import the session cookie in their own browser by using a Cookie Editor add-on. Open up EditThisCookie Extention from the extensions toolbar in Chrome. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. A tag already exists with the provided branch name. This tool is a successor toEvilginx, released in 2017, which used a custom version of nginx HTTP server to provide man-in-the-middle functionality to act as a proxy between a browser and phished website.
You can also just print them on the screen if you want. Cyber security services offered by Stroz Friedberg Inc. and its affiliates. Additionally, organizations can also help guard against attacks by providing user training on how to better identify phishing emails and malicious websites. The parameter name is randomly generated and its value consists of a random RC4 encryption key, checksum and a base64 encoded encrypted value of all embedded custom parameter. The session can be displayed by typing: After confirming that the session tokens are successfully captured, we can get the session cookies by typing: The attacker can then copy the above session cookie and import the session cookie in their own browser by using a Cookie Editor add-on. Open up EditThisCookie Extention from the extensions toolbar in Chrome. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. A tag already exists with the provided branch name. This tool is a successor toEvilginx, released in 2017, which used a custom version of nginx HTTP server to provide man-in-the-middle functionality to act as a proxy between a browser and phished website. In this case, I am using the Instagram phishlet: phishlets hostname instagram instagram.macrosec.xyz. Evilginx2 is an attack framework for setting up phishing pages. Evilginx 2 is a MiTM Attack Framework used for phishing login credentials along with session cookies. As an example, if you'd like only requests from iPhone or Android to go through, you'd set a filter like so: You can finally route the connection between Evilginx and targeted website through an external proxy. WebEvilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes. You can also add your own GET parameters to make the URL look how you want it. Phishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website.
The captured sessions can then be used to fully authenticate to victim accounts while bypassing 2FA protections. During assessments, most of the time hostname doesn't matter much, but sometimes you may want to give it a more personalized feel to it. evilginx2 google phishlet. Just set an ua_filter option for any of your lures, as a whitelist regular expression, and only requests with matching User-Agent header will be authorized.
Evilginx2 does not serve its own HTML look-alike pages like in traditional phishing attacks. These are: {lure_url}: This will be substituted with an unquoted URL of the phishing page. This blog post was written by Varun Gupta. WebToday, we are going to examine Evilginx 2, a reverse proxy toolkit. Instead of serving templates of sign-in pages lookalikes, Evilginx2 becomes a relay (proxy) between the real website and the phished user. Home > Uncategorized > evilginx2 google phishlet. In the example shown above, the IP address of the phishing server is shown in red and ends in .91, while the IP address of the mock threat actor system is shown in orange and ends in .94. I personally recommend Digital Ocean and if you follow my referral link, you willget an extra $10 to spend on servers for free. DO NOT ASK FOR PHISHLETS. FIDO2 authentication uses cryptographic keys that are pre-registered with a service such as M365 to allow the user to authenticate to that site. Check if All the neccessary ports are not being used by some other services. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. Custom parameters to be imported in text format would look the same way as you would type in the parameters after lures get-url command in Evilginx interface: For import files, make sure to suffix a filename with file extension according to the data format you've decided to use, so .txt for text format, .csv for CSV format and .json for JSON. Developed between 2018 and 2021, Evilginx2 is an open-source phishing framework that is built on an earlier framework, EvilGinx. Click on Import. You can always find the current blacklist file in: By default automatic blacklist creation is disabled, but you can easily enable it using one of the following options: This will automatically blacklist IPs of unauthorized requests. Please As you can see from the screenshot below we have successfully logged into Linked in using our stolen cookies and 2FA session keys. There is a risk of downgrade attacks on FIDO2 authentication, where alternative authentication methods are also made available. Aon and other Aon group companies will use your personal information to contact you from time to time about other products, services and events that we feel may be of interest to you. All the phishlets here are tested and built on the modified version of evilginx2: https://github.com/hash3liZer/evilginx2. This can fool the victim into typing their credentials to log into the instagram.com that is displayed to the victim by Evilginx2. -. Phished user interacts with the real website, while Evilginx2 captures all the data being transmitted between the two parties. Cybersecurity is always evolving, and the abilities of threat actors to circumvent MFA does not come as a surprise. This one is to be used inside of your Javascript code. They are the building blocks of the tool named evilginx2. Evilginx is a man-in-the-middle attack framework used for phishing credentials along with session cookies, which can then be used to bypass 2-factor authentication protection. Few sites have protections based on user agent, and relaying on javascript injections to modify the user agent on victim side may break/slow the attack process. Make sure you are using this version of evilginx: If you server is in a country other than United States, manually add the `accounts.gooogle.
Can Help regarding projects related to Reverse Proxy. This is to hammer home the importance of MFA to end users. Well quickly go through some basics (Ill try to summarize EvilGinx 2.1) and some Evilginx Phishing Examples. Evilginx is a framework and I leave the creation of phishlets to you.
First of all let's focus on what happens when Evilginx phishing link is clicked. Work fast with our official CLI. No description, website, or topics provided. We can verify if the lure has been created successfully by typing the following command: Thereafter, we can get the link to be sent to the victim by typing the following: We can send the link generated by various techniques. Pre-phish HTML templates add another step in, before the redirection to phishing page takes place. Here is a demo of what a creative attacker could do with Javascript injection on Google, pre-filling his target's details for him: Removal of landing_url section To upgrade your phishlets to version 2.3, you have to remove
 What is evilginx2? These attacks threaten more than just email environments, as other services such as Okta, Citrix, and others are at risk of the same types of attack. You may for example want to remove or replace some HTML content only if a custom parameter target_name is supplied with the phishing link. DEVELOPER DO NOT SUPPORT ANY OF THE ILLEGAL ACTIVITIES. Javascript Injection can fix a lot of issues and will make your life easier during phishing engagements. If you find any problem regarding the current version or with any phishlet, make sure to report the issue on github. While it may be difficult to positively identify the use of a proxy phishing site such as Evilginx2, there are fact patterns that examiners can rely on to indicate that an attacker may have stolen a users cookies through a phishing site. You can specify {from_name} and {filename} to display a message who shared a file and the name of the file itself, which will be visible on the download button. Even if phished user has 2FA enabled, the attacker, who has a domain and a VPS server, is able to remotely take over his/her account. Evilginx 2 is a MiTM Attack Framework used for phishing login credentials along with session cookies. On this page, you can decide how the visitor will be redirected to the phishing page. Do Not Sell or Share My Personal Information, StrozFriedbergIncident Response Services, Initial logins from the phishing server will appear as the. However, on the attacker side, the session cookies are already captured. Without a clearly anomalous user agent, the only clear indicator of compromise in the login event is the anomalous IP address.
What is evilginx2? These attacks threaten more than just email environments, as other services such as Okta, Citrix, and others are at risk of the same types of attack. You may for example want to remove or replace some HTML content only if a custom parameter target_name is supplied with the phishing link. DEVELOPER DO NOT SUPPORT ANY OF THE ILLEGAL ACTIVITIES. Javascript Injection can fix a lot of issues and will make your life easier during phishing engagements. If you find any problem regarding the current version or with any phishlet, make sure to report the issue on github. While it may be difficult to positively identify the use of a proxy phishing site such as Evilginx2, there are fact patterns that examiners can rely on to indicate that an attacker may have stolen a users cookies through a phishing site. You can specify {from_name} and {filename} to display a message who shared a file and the name of the file itself, which will be visible on the download button. Even if phished user has 2FA enabled, the attacker, who has a domain and a VPS server, is able to remotely take over his/her account. Evilginx 2 is a MiTM Attack Framework used for phishing login credentials along with session cookies. On this page, you can decide how the visitor will be redirected to the phishing page. Do Not Sell or Share My Personal Information, StrozFriedbergIncident Response Services, Initial logins from the phishing server will appear as the. However, on the attacker side, the session cookies are already captured. Without a clearly anomalous user agent, the only clear indicator of compromise in the login event is the anomalous IP address. Evilginx is smart enough to go through all GET parameters and find the one which it can decrypt and load custom parameters from. https://breakdev.org/evilginx-2-next-generation-of-phishing-2fa-tokens/, https://www.youtube.com/watch?v=PNXVhqqcZ8Y, https://www.youtube.com/watch?reload=9&v=GDVxwX4eNpU, https://www.youtube.com/watch?v=QRyinxNY0fk&t=347s. OJ Reeves @TheColonial - For constant great source of Australian positive energy and feedback and also for being always humble and a wholesome and awesome guy!
You should seeevilginx2logo with a prompt to enter commands. 10.0.0.1): Set up your servers domain and IP using following commands: Now you can set up the phishlet you want to use. FP.AGRC.238.JJ The following products or services are not regulated by the Financial Conduct Authority: Copyright 2021 Aon plc. Custom User Agent Can be Added on the fly by replacing the, Below is the work Around Code to achieve this. @an0nud4y - For sending that PR with amazingly well done phishlets, which inspired me to get back to Evilginx development.
Pole Bending Association, University Of Nottingham Graduation Gown, Articles E